Have any question?
Text or Call (954) 573-1300
Text or Call (954) 573-1300
 The value of your email account cannot be understated. You may think less of your email inbox because there are so many other ways to digitally communicate, but to a hacker, your email is a goldmine of valuable information. You may use your email less than ever before, but that doesn't mean you can neglect email security.
The value of your email account cannot be understated. You may think less of your email inbox because there are so many other ways to digitally communicate, but to a hacker, your email is a goldmine of valuable information. You may use your email less than ever before, but that doesn't mean you can neglect email security.
 Sometimes, when complex systems are put into place, the simplest and most fundamental tasks seem to be neglected. Updating your business' software should not be avoided. Software updates help secure your network and provide your company with an extra competitive edge. Don't risk your company's strengths by neglecting your software updates!
Sometimes, when complex systems are put into place, the simplest and most fundamental tasks seem to be neglected. Updating your business' software should not be avoided. Software updates help secure your network and provide your company with an extra competitive edge. Don't risk your company's strengths by neglecting your software updates!
 Installing a VPN solution is perhaps the best move you can make to ensure the security of your network, and the files that it transports. Whether you send files between your workplace and home or to remote locations around the globe, VPN can help ensure their safety. What exactly is VPN, and why should your company be using it?
Installing a VPN solution is perhaps the best move you can make to ensure the security of your network, and the files that it transports. Whether you send files between your workplace and home or to remote locations around the globe, VPN can help ensure their safety. What exactly is VPN, and why should your company be using it?
 Since the late 1990s, digital information, music, movies, software, and content has been at risk of being illegally shared worldwide for free. Peer-to-peer file sharing has forced entire industries to shift the way they do business as they try to counteract the illegal practice. The new Copyright Alert System will attempt to quell illegal file sharing.
Since the late 1990s, digital information, music, movies, software, and content has been at risk of being illegally shared worldwide for free. Peer-to-peer file sharing has forced entire industries to shift the way they do business as they try to counteract the illegal practice. The new Copyright Alert System will attempt to quell illegal file sharing.
 The latest news in office technology movements is the shift toward BYOD (Bring Your Own Device) environments; in which employees are bringing their own mobile devices to work. All the cool kids are doing it, but should you? Before you follow the trend and allow your employees to bring their devices to work, you should consider these risks.
The latest news in office technology movements is the shift toward BYOD (Bring Your Own Device) environments; in which employees are bringing their own mobile devices to work. All the cool kids are doing it, but should you? Before you follow the trend and allow your employees to bring their devices to work, you should consider these risks.
 Recently, Adobe sent out e-mails and letters to users notifying everyone of a security breach. "The attackers may have obtained access to your Adobe ID and encrypted password." The obvious question here is, "How do I protect myself and my business from such attacks?" The unfortunate answer is you can't, but you can marginalize the impact by taking some common sense measures.
Recently, Adobe sent out e-mails and letters to users notifying everyone of a security breach. "The attackers may have obtained access to your Adobe ID and encrypted password." The obvious question here is, "How do I protect myself and my business from such attacks?" The unfortunate answer is you can't, but you can marginalize the impact by taking some common sense measures.
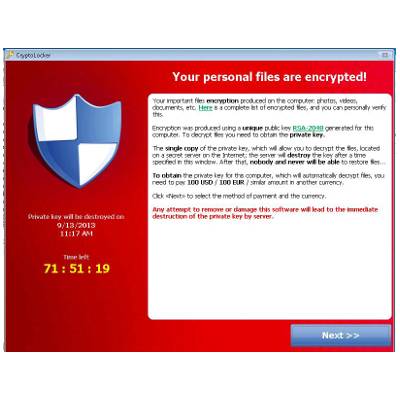 On September 10th, 2013, a new ransomware known as Trojan:Win32/Crilock.A began attacking computers all over the Internet, locking users out of their PCs and putting sensitive information at risk. If your computer gets it, then you're in for a world of hurt. Here are the details on what this virus does and what you can do to prevent it.
On September 10th, 2013, a new ransomware known as Trojan:Win32/Crilock.A began attacking computers all over the Internet, locking users out of their PCs and putting sensitive information at risk. If your computer gets it, then you're in for a world of hurt. Here are the details on what this virus does and what you can do to prevent it.
 When your network's security is doing its job and keeping your business safe, it's easy to not think about it because you don't feel the heat from any threats. Just because you're not feeling the heat, however, doesn't mean you're out of the kitchen. Even if you enjoy strong security, you will still need to perform regular security maintenances.
When your network's security is doing its job and keeping your business safe, it's easy to not think about it because you don't feel the heat from any threats. Just because you're not feeling the heat, however, doesn't mean you're out of the kitchen. Even if you enjoy strong security, you will still need to perform regular security maintenances.
 If you use a smartphone to take personal pictures and post them to the Internet, then you may unknowingly be posting more about yourself than you want to, like where and when the picture was taken. This information in the hands of the wrong person can lead to dangerous consequences, like theft of your property, your identity, or even kidnapping.
If you use a smartphone to take personal pictures and post them to the Internet, then you may unknowingly be posting more about yourself than you want to, like where and when the picture was taken. This information in the hands of the wrong person can lead to dangerous consequences, like theft of your property, your identity, or even kidnapping.
 With an increase in Distributed Denial of Service (DDOS) attacks and packet flooding volume, its evident that hackers are using compromised web servers for their malicious activities. By infecting servers, these dastardly infiltrators create a Zombie command-and-control center to direct their malicious activities from.
With an increase in Distributed Denial of Service (DDOS) attacks and packet flooding volume, its evident that hackers are using compromised web servers for their malicious activities. By infecting servers, these dastardly infiltrators create a Zombie command-and-control center to direct their malicious activities from.
 If you have been following international news headlines with stories like WikiLeaks spreading confidential documents, and recent revelations about a US surveillance scandal, it kind of feels like we are in the middle of Spy vs. Spy. As nations look for stronger security solutions to protect themselves, Russia is looking to older technology to keep their communications safe.
If you have been following international news headlines with stories like WikiLeaks spreading confidential documents, and recent revelations about a US surveillance scandal, it kind of feels like we are in the middle of Spy vs. Spy. As nations look for stronger security solutions to protect themselves, Russia is looking to older technology to keep their communications safe.
 Driving a powerful car can be an exhilarating experience, but if you have no idea what you're doing, it can be dangerous. This is why governments require drivers to pass a safety class before they can speed down the road encased in steel and glass. The Internet is also a powerful tool that can be exciting, beneficial, and dangerous.
Driving a powerful car can be an exhilarating experience, but if you have no idea what you're doing, it can be dangerous. This is why governments require drivers to pass a safety class before they can speed down the road encased in steel and glass. The Internet is also a powerful tool that can be exciting, beneficial, and dangerous.
 While there are some startup businesses reading this that have not used anything older than Windows 7, there are other companies out there that are more seasoned and have been using their computer system for decades. Legacy companies like this may have found it difficult to open old files with newer systems; here's how to fix this using Microsoft Office.
While there are some startup businesses reading this that have not used anything older than Windows 7, there are other companies out there that are more seasoned and have been using their computer system for decades. Legacy companies like this may have found it difficult to open old files with newer systems; here's how to fix this using Microsoft Office.
 As smartphone ownership continues to rise (175 million cellphones sold last year in the US), so too does smartphone theft. Take San Francisco, CA as an example, half of all robberies reported last year were phone-related. To help curb this trend, crime fighting agencies are seeking help from phone manufacturers in developing a smartphone kill switch.
As smartphone ownership continues to rise (175 million cellphones sold last year in the US), so too does smartphone theft. Take San Francisco, CA as an example, half of all robberies reported last year were phone-related. To help curb this trend, crime fighting agencies are seeking help from phone manufacturers in developing a smartphone kill switch.
 The whole purpose of having a network infrastructure is to allow different users to access and share needed files and applications. With your data centralized to a server, you will need to have a system in place that allows certain people up-to-date permissions to access needed files from every computer. This is where Active Directory comes in.
The whole purpose of having a network infrastructure is to allow different users to access and share needed files and applications. With your data centralized to a server, you will need to have a system in place that allows certain people up-to-date permissions to access needed files from every computer. This is where Active Directory comes in.
 You know that having a strong firewall is a key component to having strong network security, but do you how firewalls work? Firewalls take their name from the protective barriers that keep buildings and engines safe from fire. While it’s unlikely that your computer is in danger of incineration, a firewall does protect it from cyber-threats; here’s how!
You know that having a strong firewall is a key component to having strong network security, but do you how firewalls work? Firewalls take their name from the protective barriers that keep buildings and engines safe from fire. While it’s unlikely that your computer is in danger of incineration, a firewall does protect it from cyber-threats; here’s how!
Learn more about what L7 Solutions can do for your business.
L7 Solutions
7890 Peters Road Building G102,
Plantation, Florida 33324